In this post, I won’t be going into quite as much detail as Zack did at his workshop, but I will show you how to avoid or fix certain issues that sometimes come up when moving your WordPress site to HTTPS.
We do this type of transition for clients all the time, so hopefully we can help you avoid some of the roadblocks we’ve encountered along the way.
P.S. I’m sure you’ve heard this by now, but you need to move your website to HTTPS if you haven’t already. Not only is it a potential security risk, but you’re also actively losing visitor trust and slowing down your website, plus browsers are cracking down on HTTP sites more than ever. Even if you don’t have a shopping cart or member area on your website: PLEASE 👏 SECURE 👏 YOUR 👏 WEBSITE 👏 WITH 👏 HTTPS!
Is it easy to move to HTTPS?
First thing’s first: How easy is it to change a WordPress website from HTTP to HTTPS?
It depends. Nobody ever wants to hear that answer, but it’s the truth.
Changing a WordPress site could take anywhere from 15 minutes to a year. And if you think I’m being facetious about a year, let’s go back to my friend Zack and his adventures in HTTPS.
In 2016, Zack was tasked with moving wired.com — one of the oldest tech publications on the web — to HTTPS. In all, it took their team about 160 human hours to complete the transition. 160 incredibly intelligent human hours. In normal human hours, that’s easily a calendar year.
And sure, most of us aren’t making the transition for a site like WIRED, but it does help illustrate the point that the amount of time it takes to move your site to HTTPS depends on the type of content on your website, how long your site has been around, where your website is hosted, and a myriad of other factors.
I highly recommend you watch Zack’s talk on how they successfully made the move to HTTPS for WIRED. It’s a fantastic opportunity to learn:
Let’s talk SSL/TLS certificates
Now that we’ve got the “how long will this take?” question out of the way, it’s now time to talk about the different types of SSL/TLS certificates that are available. Short for “Secure Sockets Layer” and “Transport Layer Security,” SSL and TLS certificates are security protocols that encrypt connections between your site and your users. You need an SSL or a TLS certificate to make HTTPS happen.
Not all SSL/TLS offerings are created equal
Before getting a certificate, it’s important you understand that not all certificates are created equal. There are varying levels of validation for different purposes. This post does a great job of describing the different levels and what their purposes are without overcomplicating the issue. Here’s a quick rundown:
- DV – DV is a standard Domain Validation certificate. These certificates are what most people have on their websites.
- OV – OV is known as Organizational Validation, and requires some additional validation to make sure the website and business are real entities.
- EV – EV is an Extended Validation certificate and is the most thorough of all. This is the criminal background check equivalent of SSL/TLS certificate issuance. These are very popular among bigger corporations because they not only help with consumer trust, they also typically come with some type of financial protection from fraud. You can tell a site has an EV certificate very easily — you will see their company name next to their URL in the address bar, next to the secure lock icon.

Can I get a free SSL/TLS certificate?
If you’ve never had to deal with this stuff in the past, figuring out these certificates can be a headache as well as an unexpected expense for your business. Luckily, there is a free option out there — LetsEncrypt. This fantastic initiative offers free SSL/TLS certificates and automates the exhausting process of creating, validating, signing, installing, and renewing certificates. As a result of their affordable, streamlined process, LetsEncrypt has played a huge role in building a more secure web over the past several years.
“Free” doesn’t come without some hidden costs
Okay, yes, LetsEncrypt is fantastic! However, there are few things you should know before you start heavily drinking that LetsEncrypt Kool-Aid:
- LetsEncrypt has no validation options beyond Domain Validation. And they have no plans to implement OV or EV certificates in the future. So if your website requires a more extensive certificate, LetEncrypt may not be a suitable option for your site.
- LetsEncrypt certificates need to be renewed every three months. I totally understand why this is the case from a technical standpoint. Since they’re providing free certificates, they need to make sure they’re regularly reused and recycled. Makes sense.
- LetsEncrypt certificate renewals sometimes have issues. Even with automatic renewals in place, I’ve seen a number of instances where auto-renewals fail for one reason or another. I don’t believe it’s the fault of LetsEncrypt. It’s more than likely an issue with whoever built the auto-renewal process, but nonetheless, it is a problem we’ve seen in more than one occasion.
- Your web host may not fully support LetsEncrypt. To expand on point #3 above, a failed certificate renewal likely means downtime for your website until you can manually renew it. SiteGround is still battling a months-long issue with auto-renewals. LetsEncrypt also doesn’t offer support beyond their documentation. If you’re trying to use a LetsEncrypt certificate on your own, you’re gonna need some System Administration skills. LetsEncrypt maintains a list of all of the hosting providers that have LetsEncrypt support.
If you have a host who fully supports LetsEncrypt and their auto-renewal system, and you don’t need anything beyond Domain Validation, LetsEncrypt is definitely a strong way to go. If you’d rather purchase a certificate, or simply need an OV or EV cert, we can help with that! As with our web development and digital marketing services, you can order an SSL certificate through our parent company, Southern Web.
SSL offerings from the most popular hosting companies
I’ve put together a master chart of all the most popular hosting companies and what their SSL offering looks like. Use this data to your advantage next time you’re choosing a new web host.
CDNs and firewalls produce some fun challenges
If you’re using a content delivery network like MaxCDN or KeyCDN, or a firewall service like CloudFlare or Sucuri WAF, you’re going to want to pay attention here.
All these services require a separate certificate from the one being used on the server where your website lives. I repeat, even if you have a certificate setup to protect your website, more than likely you’re going to need to make some special configuration changes when using a CDN or Firewall.

A common occurrence we’ve seen is a client using a host like WP Engine and wants their CDN to use a hostname like cdn.domain.com. Even if they’re using the CDN provided by WP Engine, a separate certificate is required, which can really trip people up.
If you’re going down this path alone, please read the owner’s manual. You don’t want your website to end up like a sad IKEA furniture fail.
CDN and firewall resources for popular web hosts
- Setting UP Cloudflare with GoDaddy Hosting
- How to Use Sucuri at Pagely
- Configuring a Custom CNAME with MaxCDN and WP Engine
- Using KeyCDN at Kinsta
Mixed content: Are your third party scripts secure?
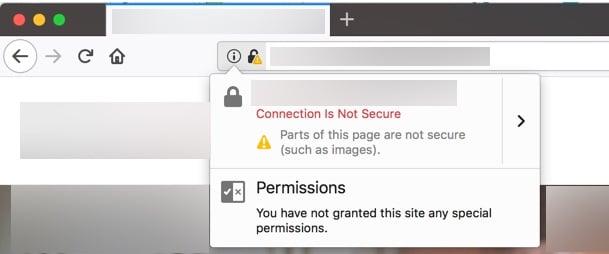
The last thing I want to address before we go our separate ways is mixed content. Mixed content is where we see the most HTTPS conversion snafus.
When moving a site to HTTPS, mixed content is that evil little nuisance that keeps browsers from displaying that satisfying green lock. People won’t necessarily get an insecure warning, but they will get some type of message indicating that some of the content on the page isn’t secure.
There are WordPress plugins that try and correct mixed content errors, but they can only do so much.
Primary mixed content culprits
There are three places that typically contribute to mixed content issues:
- Incomplete database URL replacement. When moving to HTTPS, we recommend replacing all the instances of http on the site (for your domain), with HTTPS. The folks at Delicious Brains have a great guide to follow for this, but sometimes things get missed and will cause mixed content issues.
- Ads and other third party scripts. The most common mixed content errors come from third parties. Occasionally (gratefully it’s happening less and less) third-party ad providers, library providers, or other service providers won’t have support for HTTPS at all. This is becoming much less common as HTTPS becomes more prevalent, but there was a long stretch where third party scripts would consistently cause mixed content issues.
- Legacy embeds. Legacy embeds are tricky because you don’t know they’re a problem until you manually review your content. Perhaps you have an old embed for a defunct slideshow provider, or an old video service that’s still sticking around from the good ol’ days of the internet. Forcing HTTPS in these instances will break the video or audio embed, so sometimes manual review and moving content can be required. Screaming Frog is a fantastic tool that has an Insecure Content finder. It reviews all of your site URLs and identifies any mixed content.
Dealing with mixed content issues can be extremely time-consuming depending on the size and age of your website. Don’t let it get you down. Now you have the tools you need be basking in the warm glow of that bright green padlock.
Locking it down

Do you see what I did there?
We’ve covered the most common issues you’ll encounter when moving to HTTPS with WordPress. I’ve also included some additional resources below if you want to take the DIY route here. If you’d like to hire pros, we’d be happy to get you a quick estimate. You can get in touch with our team right here. We’d love to help!
Other HTTPS resources
- Updating email captures and forms
- Implementing 301 redirects with NGINX, Varnish, or Apache
- Registering a new HTTPS website with Google Search Console
Questions? Anything I missed?
If we can be of any help at all, hit us up in the comments. We love the discussion!





